VIDEO
Bhawna Dua (Engineering Program Manager at Proofpoint) and Shalini Sundaram (Group Product Manager at Proofpoint) encourage women to make a career transition into the cybersecurity, an industry that is trending and is practically recession proof! Bhawna and Shalini will provide insight into their career journeys to share perspective.
Like what you see here? Our mission-aligned Girl Geek X partners are hiring!
- Check out open jobs at our trusted partner companies.
- Watch all ELEVATE 2023 conference video replays!
- Does your company want to sponsor a Girl Geek Dinner? Talk to us!

Sukrutha Bhadouria: I am now here to introduce Bhawna and Shalini from Proofpoint. Bhawna is a senior engineering program manager at Proofpoint. Shalini is a group product manager at Proofpoint. We will now be hearing from both these ladies on their unique journeys to cybersecurity and how you too can begin a career in cybersecurity. Welcome, Bhawna and Shalini.
Bhawna Dua: Thank you Sukrutha for the introduction, and thank you folks for joining our talk, demystifying cybersecurity. Today, me and my counterpart, Shalini, would like to shed some light on the somewhat mysterious field of cybersecurity and highlight why it is a good career choice for the times that we live in. In the last few years, we’ve been hearing a lot about these security breaches and hacks. Shalini, why do you think these matters so much, especially to us as individuals?
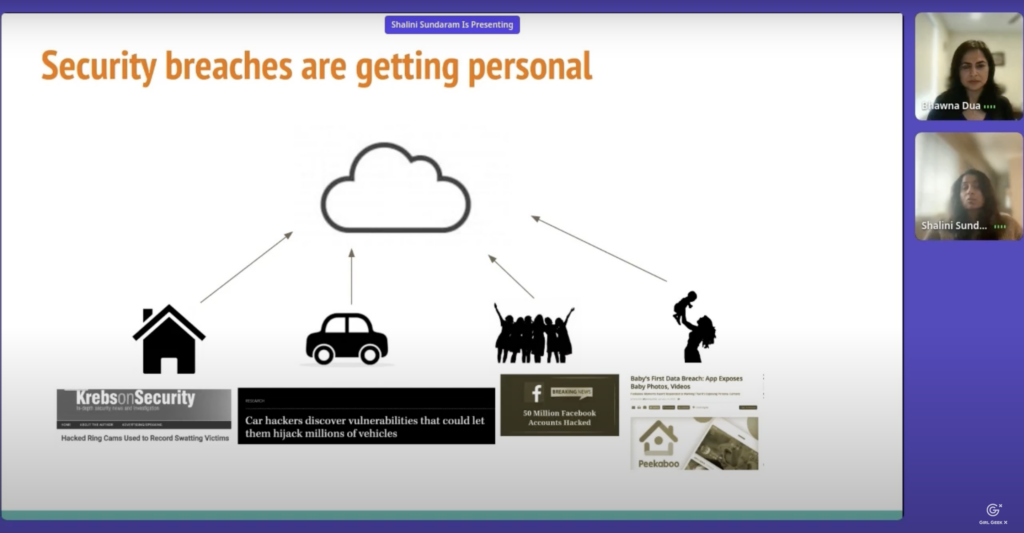
Shalini Sundaram: Yeah, that’s a great question, partner. We’ve actually seen tremendous progress in the field of cloud computing and IOT in the last few years, right? And what that means for us is really a life of luxury, right? We can answer our doorbells sitting in the kitchen. We can warm up our car seats before we go for a drive. We can have day-to-day conversations with our friends and our relatives across the globe. And my personal favorite is we can actually store and retrieve our most fondest memories right in the fraction of the second. But while the world has become a more connected and a more convenient place for us all to live in, we are seeing that it’s now turned into a gold mine for attackers, right?
Shalini Sundaram: We’ve seen attacks ranging from small pranks all the way to more serious risks where car hackers hijack millions of vehicles and they can control where you drive. We’ve all heard about the Facebook hack, right? All of our personal details were exposed to the world. But what’s very disturbing to me is that some of our most precious moments, like our babies’ first steps, even those are now under attack. But Bhawna, it’s not just us as individuals who are getting impacted by this. We also see enterprises are facing the brunt of this. Don’t you think that the cyber crimes have been increasing?
Bhawna Dua: Absolutely. You are right. Shalani. The rise in cyber crimes itself has been exponential resulting in an equivalent increase in the cost. In 2015, the cost of cyber crimes was around 3 trillion. It doubled itself by 2021 to 6 trillion, and now it is projected that by 2025, it is going to be around 10.5 trillion. Now, these costs include things like theft of intellectual property, personal and financial data, as well as the cost of fraud and reputational harm, just to name a few. As you can anticipate, the demand for cybersecurity professionals is rapidly increasing, and it is projected that by 2025, there will be 3.5 million fewer cybersecurity professionals than the actual number of available jobs. Shalini, how about we give our audience a little bit of insight into a couple of these hacks or attacks and how things unfolded? You have an interesting example to share with us today about software supply chain compromise, right?
Shalini Sundaram: Yeah, that’s right, Bhawna. The SolarWinds hack – this actually happened in 2020, right? The security community community is still talking about it because if you look at most attacks, they go after one organization. What these attackers did is they went after one company that whose, whose products are being used by thousands of organizations, right? The attackers introduced malicious code into one of the software updates, and 18,000 organizations ended up downloading it. 20% of those institutions included federal ones, right? The Department of Homeland Security, Department of Energy, and it took them over a year to actually discover the attack. As you can see, this was a pretty sophisticated attack.
Shalini Sundaram: Let’s go a little bit behind the scenes to see how the attackers did this. The actors who were behind this was a Russian group called Cozy Bear, and the first thing that they did is they got onto the code base of SolarWinds. They introduced malicious code into one of the software libraries that was being used as part of the update. And this malicious update went out to thousands of organizations. SolarWinds in the meanwhile, was absolutely oblivious to all of this stuff because they didn’t have any security tools that were monitoring their code base for malware. Now, after the updates got pushed out, it’s not like the attackers a acted immediately, right? They took their own time and they were not after these small financial gains. So what they did was they actually monitored all the systems and they were looking for software products, right? They were figuring out which versions were running so that they can identify vulnerabilities in them. Similarly, they were trying to figure out which security products were running so that they can figure out how to evade them.
Shalini Sundaram: Using all these attacker technique, they maintain a very low footprint and they ended up uploading a lot of confidential data, right? And some of that data also included details about the sanctions that the US had posed against Russia. The big takeaway here, right, is that attackers are getting more and more sophisticated and the scale of impact that they have is increasing. But we also saw another attack where these threat actors, they were bold enough to go after critical security infrastructure. Could you give us a little bit insight about that?
Bhawna Dua: Yes, sure. Thanks, char. This was the Saudi Aramco attack, and it was very interesting in the sense that it highlights the threat to our critical infrastructure. To give a little bit of background, the target of this attack was an oil and gas company in Saudi Arabia, in which this huge oil company, Aramco had a big stake.
Bhawna Dua: Now, the attackers targeted an industrial control system using what we call a multi-stage malware. This malware was injected using either a phishing email or a physical USB stick into the company’s network. Now, what was this malware capable of? It could spin the rotating parts of the control system and make it unstable so that eventually the machine would break. And if that machine or equipment breaks, it actually means a loss of life. Now, the reason this attack did not fully materialize was due to a slight misconfiguration on the part of the attackers.
Bhawna Dua: This error actually caused the fail safe mode of the equipment to trigger. And as soon as that anomaly was detected, the whole equipment shut down. Now, obviously that meant a loss of productivity, but it did not at that point mean a loss of life. Now, why does it matter so much? Because this same control system that was targeted is used in thousands of plants across the United States, thus highlighting a major threat to our critical infrastructure. Further analysis revealed that the complete file library of this malware was constructed using five different programming languages, as well as it took more than a year to build the entire malware. So you can imagine to build something of this scale and sophistication needs a huge amount of resources, which obviously points a finger to some nation state.
Bhawna Dua: Now what’s the main lesson here that we need to do much more to protect our critical infrastructure? So Shalini, let’s assume that a few folks from our audience are actually thinking to transition to cybersecurity and help solve some of these very, very difficult problems and prevent some of these crazy attacks. How would we talk a little bit about our career journeys and how we landed in cybersecurity? Let’s hear about your career part first.
Shalini Sundaram: Yeah, sure, that sounds good. My first exposure to cybersecurity was when I took a couple of courses in grad school. I got introduced to cybersecurity when I was part of my computer science program. But what was really interesting is we had a hands-on lab where we were asked to attack each other’s systems. And that was really exciting and I loved it, right? That was the moment I decided, okay, I’m definitely gonna get into cybersecurity.
Shalini Sundaram: One of the early moves that I did was I jumped into a cybersecurity startup. And being in a startup, I had the luxury to wear multiple hats. One day I would be sitting next to the security researcher, right? And we would figure out how to set up the infrastructure so that we can attract attackers and actually study their behavior, right? The next day I would also spend time with the business development team and talk to various security companies trying to understand their use cases and figuring out how we could integrate better with each other.
Shalini Sundaram: One of the things that I remember from my experience at this company was it was my very first cybersecurity conference. And at the on, on there was, this was in 2015, and there were about 400 security companies, right? But then the very next year in 2016, it doubled to 800. I could really see that the security industry was expanding rapidly. And in the next few years, I saw that it was in just that the security industry alone was expanding, but it was also making an impact on the other domains as well. For example, I was working on this networking product, right?
Shalini Sundaram: And it was leveraging a latest networking technology called software defined networking, right? And we were actually able to convince customers that even though this technology was super helpful and growing at the rate of 40% year over year, it still had some major security flaws and they couldn’t deploy it without that.
Shalini Sundaram: All of a sudden we saw the whole security industry and the networking industry kind of collide, right? So we saw the networking guys try to implement security features. And then from our side, we were trying to implement networking features. And we actually ended up hiring quite a few networking professionals to help understand that side of things. And in my current role now, right, I been exposed to multiple other domains, right? Whether it’s endpoint or whether it’s the more recent ones like cloud.
Shalini Sundaram: But what really has left an impression on me is my role as a product manager has taught me that I have to work with so many different individuals in order to build a good security product. For example, Bhawna, when, when things are when attackers change their techniques, right? Like the ones that we saw with solar, wind we have to respond immediately, right? We have to work with people like you so that we can ship our software quickly. Similarly, I have to work very closely with the user experience team so that we are able to develop products that are more intuitive to u to the, to the customer, and they’re not wasting time figuring out how the product works, right? I also have to work with sales and marketing so that they understand the value of our product so that in turn the CISOs, they can explain to their board and their CEO why they need to spend more on cybersecurity, right?
Shalini Sundaram: I guess I would say over the last few years, or like the last 15 years in cybersecurity, I’ve kinda become a little bit wise. And I feel that all you really need to be honest, is a good heart to make the right kinda impact in cybersecurity and, and Bhawna, I think this was a very traditional path for me, right? I came from the computer science program and I jumped across various cybersecurity industries, but you were from a completely different background and you ended up in cybersecurity and it was a bit of a non-traditional path. Could you give us a little bit about what you went through?
Bhawna Dua: Sure thing. Shalini, thank you for sharing your journey. Very inspiring. Well, absolutely. My background is in electrical engineering, and that’s where actually I spent the first nine years of my career, I was working at Schneider Electric in an electrical engineering capacity. And my life at that point was, you know, about these equipments like generators, transformers, uninterruptable, power supplies, or you know, things, all the things that you find in a data center. Now, while I was there, I decided to get my m MBA and started thinking about making a change. Basically, what is it that I want to do in my career next? Now this was around 20 13, 20 14, and it was a very dynamic time. And the reason I say that, because digitization was really picking steam, I took a few classes on disruptive technologies and digitization and did some extensive research in these areas.
Bhawna Dua: The three technical innovations of that time that really stood out to me were one, internet of things (IOT). We had now these billions of devices that were collecting tons of data. Second big data itself, the new data generated every year by these devices was growing by trillions of gigabytes and third cloud computing that reflected the movement of this huge amount of data as well as applications to the cloud. Now, during my research, one thing that I was discovered was that all these areas are profoundly impacted by one thing, cybersecurity. Imagine one of your IOT devices like your Ring camera or your Ring doorbell or your digitized fridge is not protected properly, and the hackers use that to get into your home network and access all the information. Imagine the kind of information we store in the cloud. It could be financial records, health data, personal information.
Bhawna Dua: If that data falls into wrong hands, it can be used for all kinds of nefarious purposes. So for me, that was enough motivation. I felt it is an opportunity to make a real difference as well as do good at the same time. Now, the key was how do I make this transition from electrical engineering into the cyber world? During my time at Schneider, one thing that I had done was build a strong base in project and program management and data analytics. And these skills are very transferrable. I thought, how about I leverage these skills along with my MBA and look for a role in cybersecurity that values what I bring to the table, but at the same time gives me an opportunity to learn about a new area? Simultaneously, I started reading a lot on cybersecurity to increase my basic understanding. I did take me some time and a few rejections to really fine tune my message and eventually land a role as a business operation analyst in a onsumer business unit.
Bhawna Dua: Now, at this point, I was really surrounded by cybersecurity professionals and started building some practical understanding in this area. A year later, I was able to transfer into a proper program manager role supporting the development and launch of products in the areas of consumer security and identity protection. Then in 2021, I decided to make a pivot because I wanted to learn a bit more about the enterprise side of cybersecurity. I joined Proofpoint and in my current role, I am supporting development of email security products and gaining some good knowledge and understanding of this domain.
Bhawna Dua: Folks, my main message is if you are thinking of making a leap, put in the hard work, identify your transferable skills, and take a calculator risk and believe that everything will work out in the end. So those were basically our journeys. Now let’s say if you are thinking of making this transition sh and I have a few next steps identified for you.
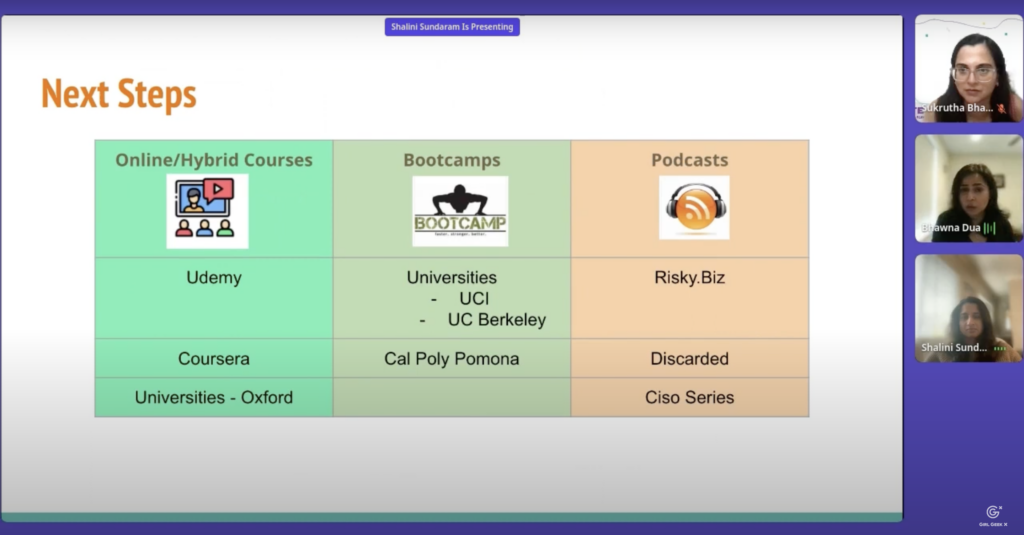
Bhawna Dua: The first one is definitely to increase your knowledge, and you can do that either by taking online or hybrid courses using one of these platforms that we have identified. If you’re looking to get into more technical stuff, then some of the universities, the very good ones, offer these six month boot camps like UCI, UC Berkeley, and to keep your knowledge up to date on an ogoing basis, Shalini and I and a lot of other cybersecurity professionals leverage podcasts. We have listed some of the good ones here. Discarded is our own Proofpoint podcast, and there are many more, so by all means, please do your research and you will find a lot of resources that are available to increase your knowledge.
Shalini Sundaram: This is a great list, Bhawna, and CISO series is my personal favorite. Well, if you found this interesting, you can read a little bit more about the other cybersecurity companies and maybe get started on your security career! Thank you so much for listening, everyone.
Bhawna Dua: Thank you ladies. This was amazing. Yeah, thank you guys. And in case you have any thank you
Shalini Sundaram: Questions?
Bhawna Dua: In case you have any questions, please feel free to reach out and Shalini and I will try to help you with whatever information we have. Thank you.
Like what you see here? Our mission-aligned Girl Geek X partners are hiring!
- Check out open jobs at our trusted partner companies.
- Watch all ELEVATE 2023 conference video replays!
- Does your company want to sponsor a Girl Geek Dinner? Talk to us!


